Policy standards overview
Draft Version 0.1, March 29, 2004
Yuri Demchenko <demch@science.uva.nl>
This memo provides very basic overview of existing policy formats with the goal to identify possible option for future refactoring of the AAA Policy language.
1. WS-Policy Framework
WS-Policy Framework (WSPolicy) provides a general purpose model and corresponding syntax to describe and communicate policies of a Webs service.
WSPolicy defines three components:
- Policy expressions
- Policy assertions
- Policy operations
Policy comprises of policy expressions (element PolicyExpressions) that may contain one of policy operations (“OneOrMore”, “All”, “ExactlyOne”), policy assertions (element PolicyAssertion) or policy reference (element PolicyReference). Policy operations can be nested and may contain any externally defined content.
The PolicyExpressions element can be used as a container for actual application/service-type specific policies definition.
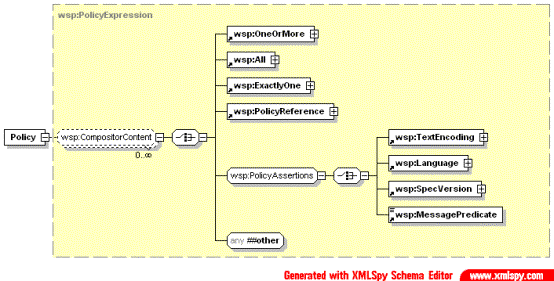
Fig. 1.1. Policy definition container in WS-Policy
WSPolicy is complemented by other WS and WS-Security specifications:
- WS-PolicyAssertions – defines policy assertions that includes assertions for TextEncoding, Language, SpecVersion, MessagePredicate
- WS-PolicyAttachment – defines three specific attachment mechanisms for using policy expressions with existing XML WS technologies (arbitrary resources, WSDL type definitions, UDDI entries)
- WS-SecurityPolicy – defines WS-Security policy extensions to WSPolicy that include the following assertions: SecurityToken, Integrity, Confidentiality, Visibility, Security Header, MessageAge.
WSPolicy set can be combined and interact with all other components of WS and WS-Security specifications. All WS-Security components are also using WS-Security extensions (WSSE) and WS-Utility (WSU).
Other important WS-Security specifications such as WS-Federation, WS-Trust and WS-SecureConversation are actively using WSPolicy and other WS-Security specifications.
WS-Trust that enables Web Services to request and issue security tokens and to manage trust relationships.
WS-SecureConversation defines extensions for secure communication by establishing and sharing security contexts, and deriving session keys from security contexts.
WS-Federation introduces well-defined mechanisms and procedures for mapping trusted information about users from one domain into authentication and authorisation information required by resource or service provider from other domain. The functionality provided by WS-Federation is similar to identity federation functionality provided by Liberty Alliance Project however it is more naturally integrated with other components of WS-Security framework.
2. XACML Policy format
XACML (eXtensible Access Control Markup Language) defines reach policy format for access control based on “Subject-Resource-Action” triad attributes. XACML defines format for policy and request/response messages.
Decision request sent in a Request message provides context for policy-based decision. The complete policy applicable to a particular decision request may be composed of a number of individual rules or policies. Few policies may be combined to form the single policy applicable to the request.
XACML defines three top-level policy elements: <Rule>, <Policy> and <PolicySet>. The <Rule> element contains a Boolean expression that can be evaluated in isolation, but that is not intended to be accessed in isolation by a PDP. So, it is not intended to form the basis of an authorization decision by itself. It is intended to exist in isolation only within an XACML PAP, where it may form the basic unit of management, and be re-used in multiple policies.
The <Policy> element contains a set of <Rule> elements and a specified procedure for combining the results of their evaluation. It is the basic unit of policy used by the PDP, and so it is intended to form the basis of an authorization decision.
The <PolicySet> element contains a set of <Policy> or other <PolicySet> elements and a specified procedure for combining the results of their evaluation. It is the standard means for combining separate policies into a single combined policy.
XACML defines a number of Rule and Policy combining algorithms that define a procedure for arriving at an authorization decision given the individual results of evaluation of a set of rules or policies, in particular:
- Deny-overrides,
- Permit-overrides,
- First applicable,
- Only-one-applicable.
XAML Policies are based (or bound) to subject and resource attributes that are different from their identities. XAML allows multiple subjects and multi-valued attributes. XAML also allows policies based on resource content what means that authorisation decision may be based on content of the requested resource or its status.
Information security policies operate upon attributes of subjects, the resource and the action to be performed on the resource in order to arrive at an authorization decision. In the process of arriving at the authorization decision, attributes of many different types may have to be compared or computed. XACML includes a number of built-in functions and a method of adding non-standard functions. These functions may be nested to build arbitrarily complex expressions. This is achieved with the <Apply> element. The <Apply> element has an XML attribute called FunctionId that identifies the function to be applied to the contents of the element. Each standard function is defined for specific argument data-type combinations, and its return data-type is also specified.
Figure 2.1 below shows data-flow for the policy-based decision making based on XACML which to large extent corresponds to the standard policy-based authorisation.
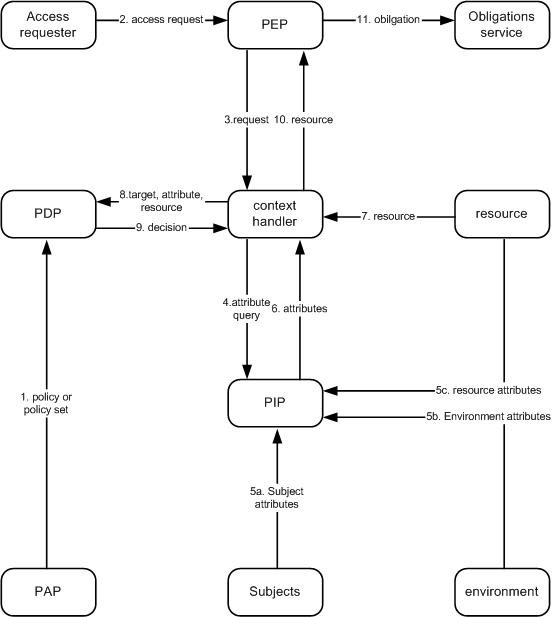
Fig. 2.1. Data-flow for the policy-based decision making based on XACML
Legend:
PAP (Policy administration point) - The system entity that creates a policy or policy set Policy-combining algorithm - the procedure for combining the decision and obligations from multiple policies
PDP (Policy decision point) - The system entity that evaluates applicable policy and renders an authorization decision
PEP (Policy enforcement point) - The system entity that performs access control, by making decision requests and enforcing authorization decisions
PIP (Policy information point) - The system entity that acts as a source of attribute values
The model operates by the following steps.
1. PAPs write policies and policy sets and make them available to the PDP. These policies or policy sets represent the complete policy for a specified target.
2. The access requester sends a request for access to the PEP.
3. The PEP sends the request for access to the context handler in its native request format,
optionally including attributes of the subjects, resource and action. The context handler
constructs an XACML request context in accordance with steps 4,5,6 and 7.
4. Subject, resource and environment attributes may be requested from a PIP.
5. The PIP obtains the requested attributes.
6. The PIP returns the requested attributes to the context handler.
7. Optionally, the context handler includes the resource in the context.
8. The context handler sends a decision request, including the target, to the PDP. The PDP identifies the applicable policy and retrieves the required attributes and (optionally) the resource from the context handler. The PDP evaluates the policy.
9. The PDP returns the response context (including the authorization decision) to the context handler.
10. The context handler translates the response context to the native response format of the PEP. The context handler returns the response to the PEP.
11. The PEP fulfills the obligations.
12. (Not shown) Finally, if access is permitted, then the PEP permits access to the resource; otherwise, it denies access.
Figure 2.2 presents the Policy language model.
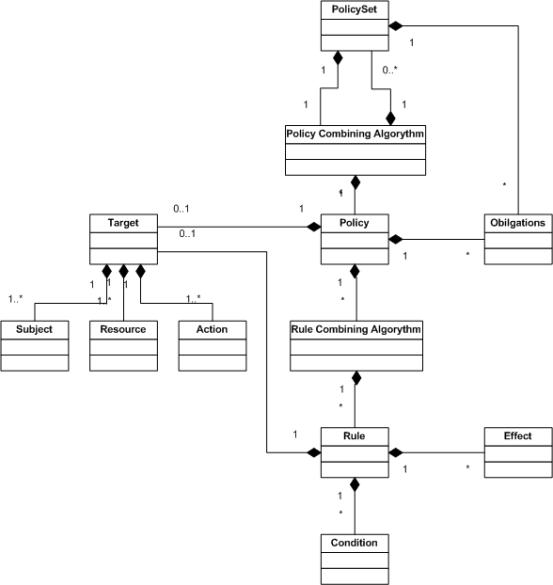
Fig. 2.2. Policy language model allowing Policies and Rules combining.
Figures 2.3 and 2.4 shows the structure of Policy element and Rule element. Policy is bound to the Target that is described by Subject, Resource and Action. Policy may contain a number of rules defined by multiple Rule elements.
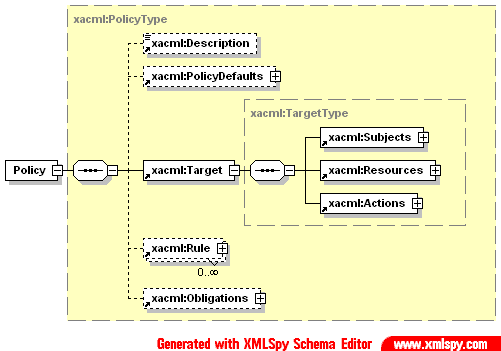
Fig. 2.3. Definition of the Policy element in XACML binding access rules to the Target (Subject, Resource, Action).
A rule is the most elementary unit of policy. The main components of a rule are target, condition that are represented by subelements and effect which is included as an attribute of the Rule element.
The <Condition> element is a boolean function over subject, resource, action and environment attributes or functions of attributes. If the <Condition> element evaluates to "True", then the enclosing <Rule> element is assigned its Effect value. The <Condition> element is of ApplyType complex type.
The <Apply> element denotes application of a function to its arguments, thus encoding a function call. The <Apply> element can be applied to any combination of<Apply>, <AttributeValue>, <SubjectAttributeDesignator>, <ResourceAttributeDesignator>, <ActionAttributeDesignator>, <EnvironmentAttributeDesignator> and <AttributeSelector> arguments.
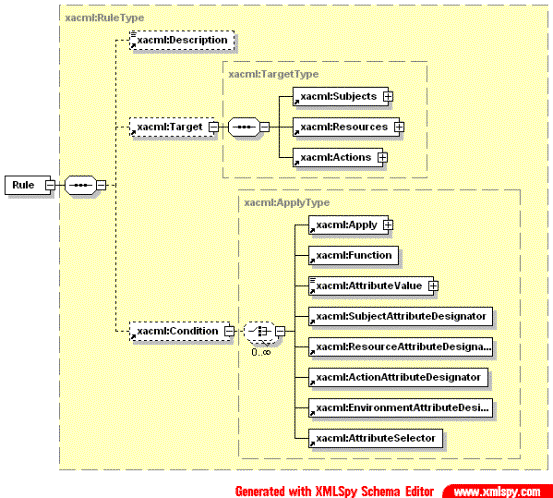
Fig. 2.4. Definition of the Rule element in XACML defining the access Conditions to the Target (Subject, Resource, Action).
XACML re-uses enumerated list of functions and operations defined in XPath 2.0 and Xquery 1.0. Complete list of functions defined for FunctionId attribute of the <Apply>/<Condition> element is provided in Appendix B.
Element Target contains matching specification for the attributes of the Subject, Resource and Action. The structure of these elements are as shown on Fig. 2.5.
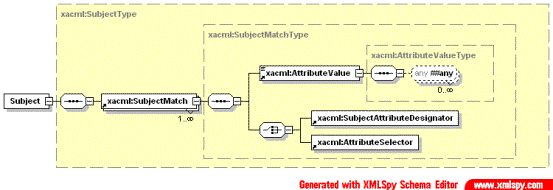
Fig. 2.5. Definition of the Subject/SubjectMatch element in XACML.
XAML defines format for the Request message that provides context for the policy-based decision. Request may contain multiple Subject elements and multiple attributes of the Subject, Resource and Action.
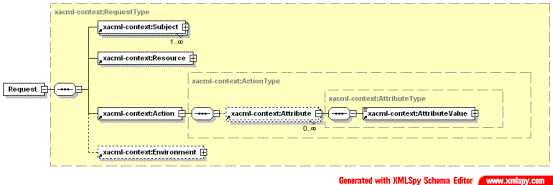
Fig. 2.6.
High-level sub-elements of the XACML Request element
Response message defined by XACML provides format for conveying Decision (“Deny” or “Permit”) and Status of the decision making process.
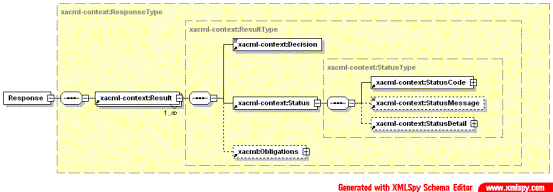
Fig. 2.7.
High-level sub-elements of the XACML Response element
2. PERMIS Policy format
PERMIS (2000-2001) proposed a policy format for X.509 Privilege Management Infrastructure that defines a set of policies (see picture Fig. 3.1):
· SubjectPolicy
· RoleHierarchyPolicy
· SOAPolicy
· RoleAssignmentPolicy
· TargetPolicy
· ActionPolicy
· TargetAccessPolicy
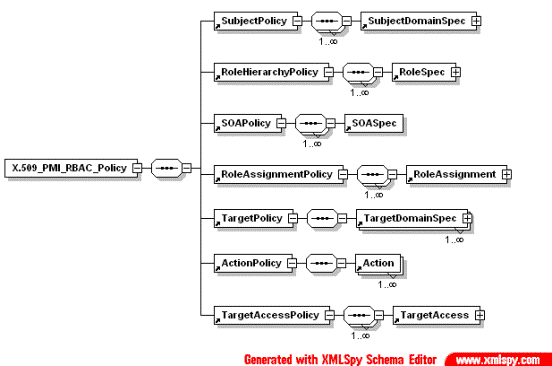
Fig. 3.1. Structure of the root element X.509_PMI_RBAC_Policy
Target Access policy includes three elements:
- Roles list RoleList
- Targets list TargetList
- Operator “IF”
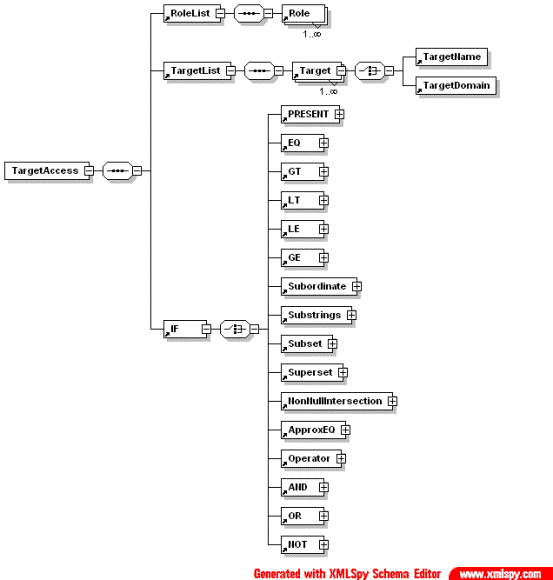
Fig. 3.2. Construction of the TargetAccess element
Operator “IF” may contain operations PRESENT, EQ, GT, LT, LE, GE, Subordinate, Substrings, Subset, Superset, NonNullIntersection, ApproxEQ, Operator, AND, OR, NOT, which AND, OR and NOT can contain cascaded “IF” elements.
Appendix A. Attributes identifiers for XACML Policy and Rule expression
A.1. Identifiers for rule- and policy combining algorithms
Rule- and policy combining algorithms are included as mandatory algorithms in the PolicySet and Policy elements respectfully.
<xs:element name="PolicySet" type="xacml:PolicySetType"/>
<xs:complexType name="PolicySetType">
<xs:sequence>
<xs:element ref="xacml:Description" minOccurs="0"/>
<xs:element ref="xacml:PolicySetDefaults" minOccurs="0"/>
<xs:element ref="xacml:Target"/>
<xs:choice minOccurs="0" maxOccurs="unbounded">
<xs:element ref="xacml:PolicySet"/>
<xs:element ref="xacml:Policy"/>
<xs:element ref="xacml:PolicySetIdReference"/>
<xs:element ref="xacml:PolicyIdReference"/>
</xs:choice>
<xs:element ref="xacml:Obligations" minOccurs="0"/>
</xs:sequence>
<xs:attribute name="PolicySetId" type="xs:anyURI" use="required"/>
<xs:attribute name="PolicyCombiningAlgId" type="xs:anyURI" use="required"/>
</xs:complexType>
<xs:element name="Policy" type="xacml:PolicyType"/>
<xs:complexType name="PolicyType">
<xs:sequence>
<xs:element ref="xacml:Description" minOccurs="0"/>
<xs:element ref="xacml:PolicyDefaults" minOccurs="0"/>
<xs:element ref="xacml:Target"/>
<xs:element ref="xacml:Rule" minOccurs="0" maxOccurs="unbounded"/>
<xs:element ref="xacml:Obligations" minOccurs="0"/>
</xs:sequence>
<xs:attribute name="PolicyId" type="xs:anyURI" use="required"/>
<xs:attribute name="RuleCombiningAlgId" type="xs:anyURI" use="required"/>
</xs:complexType>
The XACML implementation MUST include the rule- and policy-combining algorithms PolicyCombiningAlgId@PolicySet and RuleCombiningAlgId@Policy associated with the following identifiers:
urn:oasis:names:tc:xacml:1.0:rule-combining-algorithm:deny-overrides
urn:oasis:names:tc:xacml:1.0:policy-combining-algorithm:deny-overrides
urn:oasis:names:tc:xacml:1.0:rule-combining-algorithm:permit-overrides
urn:oasis:names:tc:xacml:1.0:policy-combining-algorithm:permit-overrides
urn:oasis:names:tc:xacml:1.0:rule-combining-algorithm:first-applicable
urn:oasis:names:tc:xacml:1.0:policy-combining-algorithm:first-applicable
urn:oasis:names:tc:xacml:1.0:policy-combining-algorithm:only-one-applicable
A.2. Target and Request related attribute identifiers
The implementation MUST use the attributes associated with the following identifiers in the way XACML has defined. This requirement pertains primarily to implementations of a PAP (Policy Administration Point) or PEP (Policy Enforcement Point) that use XACML, since the semantics of the attributes are transparent to the PDP (Policy Decision Point).
Subject related attributes are used in the SubjectAttributeDesignator element:
<xs:element name="SubjectAttributeDesignator" type="xacml:SubjectAttributeDesignatorType"/>
<xs:complexType name="SubjectAttributeDesignatorType">
<xs:complexContent>
<xs:extension base="xacml:AttributeDesignatorType">
<xs:attribute name="SubjectCategory" type="xs:anyURI" use="optional" default="urn:oasis:names:tc:xacml:1.0:subject-category:access-subject"/>
</xs:extension>
</xs:complexContent>
</xs:complexType>
urn:oasis:names:tc:xacml:1.0:subject:authn-locality:dns-name
urn:oasis:names:tc:xacml:1.0:subject:authn-locality:ip-address
urn:oasis:names:tc:xacml:1.0:subject:authentication-method
urn:oasis:names:tc:xacml:1.0:subject:authentication-time
urn:oasis:names:tc:xacml:1.0:subject:key-info
urn:oasis:names:tc:xacml:1.0:subject:request-time
urn:oasis:names:tc:xacml:1.0:subject:session-start-time
urn:oasis:names:tc:xacml:1.0:subject:subject-id
urn:oasis:names:tc:xacml:1.0:subject:subject-id-qualifier
urn:oasis:names:tc:xacml:1.0:subject-category:access-subject
urn:oasis:names:tc:xacml:1.0:subject-category:codebase
urn:oasis:names:tc:xacml:1.0:subject-category:intermediary-subject
urn:oasis:names:tc:xacml:1.0:subject-category:recipient-subject
urn:oasis:names:tc:xacml:1.0:subject-category:requesting-machine
The Resource, Action and Environment elements use common AttributeDesignator element with AttributeId attribute:
<xs:element name="ResourceAttributeDesignator" type="xacml:AttributeDesignatorType"/>
<xs:element name="ActionAttributeDesignator" type="xacml:AttributeDesignatorType"/>
<xs:element name="EnvironmentAttributeDesignator" type="xacml:AttributeDesignatorType"/>
<!---->
<xs:complexType name="AttributeDesignatorType">
<xs:attribute name="AttributeId" type="xs:anyURI" use="required"/>
<xs:attribute name="DataType" type="xs:anyURI" use="required"/>
<xs:attribute name="Issuer" type="xs:string" use="optional"/>
<xs:attribute name="MustBePresent" type="xs:boolean" use="optional" default="false"/>
</xs:complexType>
urn:oasis:names:tc:xacml:1.0:resource:resource-location
urn:oasis:names:tc:xacml:1.0:resource:resource-id
urn:oasis:names:tc:xacml:1.0:resource:scope
urn:oasis:names:tc:xacml:1.0:resource:simple-file-name
urn:oasis:names:tc:xacml:1.0:action:action-id
urn:oasis:names:tc:xacml:1.0:action:implied-action
A.3. Status codes defined in XACML Response message format
Status code is reported in the Decision/Status/StatusCode of the Response message. Implementation support for the urn:oasis:names:tc:xacml:1.0:context:status element is optional, but if the element is supported, then the following status codes must be supported and must be used in the way XACML has specified.
urn:oasis:names:tc:xacml:1.0:status:missing-attribute
urn:oasis:names:tc:xacml:1.0:status:ok
urn:oasis:names:tc:xacml:1.0:status:processing-error
urn:oasis:names:tc:xacml:1.0:status:syntax-error
Appendix B. <xaml:Apply ...> FunctionId attribute enumeration
Note. XACML re-uses enumerated list of functions and operations defined in XPath 2.0 and Xquery 1.0
urn:oasis:names:tc:xacml:1.0:function:string-equal
urn:oasis:names:tc:xacml:1.0:function:boolean-equal
urn:oasis:names:tc:xacml:1.0:function:integer-equal
urn:oasis:names:tc:xacml:1.0:function:double-equal
urn:oasis:names:tc:xacml:1.0:function:date-equal
urn:oasis:names:tc:xacml:1.0:function:time-equal
urn:oasis:names:tc:xacml:1.0:function:dateTime-equal
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-equal
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-equal
urn:oasis:names:tc:xacml:1.0:function:anyURI-equal
urn:oasis:names:tc:xacml:1.0:function:x500Name-equal
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-equal
urn:oasis:names:tc:xacml:1.0:function:hexBinary-equal
urn:oasis:names:tc:xacml:1.0:function:base64Binary-equal
urn:oasis:names:tc:xacml:1.0:function:integer-add
urn:oasis:names:tc:xacml:1.0:function:double-add
urn:oasis:names:tc:xacml:1.0:function:integer-subtract
urn:oasis:names:tc:xacml:1.0:function:double-subtract
urn:oasis:names:tc:xacml:1.0:function:integer-multiply
urn:oasis:names:tc:xacml:1.0:function:double-multiply
urn:oasis:names:tc:xacml:1.0:function:integer-divide
urn:oasis:names:tc:xacml:1.0:function:double-divide
urn:oasis:names:tc:xacml:1.0:function:integer-mod
urn:oasis:names:tc:xacml:1.0:function:integer-abs
urn:oasis:names:tc:xacml:1.0:function:double-abs
urn:oasis:names:tc:xacml:1.0:function:round
urn:oasis:names:tc:xacml:1.0:function:floor
urn:oasis:names:tc:xacml:1.0:function:string-normalize-space
urn:oasis:names:tc:xacml:1.0:function:string-normalize-to-lower-case
urn:oasis:names:tc:xacml:1.0:function:double-to-integer
urn:oasis:names:tc:xacml:1.0:function:integer-to-double
urn:oasis:names:tc:xacml:1.0:function:or
urn:oasis:names:tc:xacml:1.0:function:and
urn:oasis:names:tc:xacml:1.0:function:n-of
urn:oasis:names:tc:xacml:1.0:function:not
urn:oasis:names:tc:xacml:1.0:function:present
urn:oasis:names:tc:xacml:1.0:function:integer-greater-than
urn:oasis:names:tc:xacml:1.0:function:integer-greater-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:integer-less-than
urn:oasis:names:tc:xacml:1.0:function:integer-less-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:double-greater-than
urn:oasis:names:tc:xacml:1.0:function:double-greater-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:double-less-than
urn:oasis:names:tc:xacml:1.0:function:double-less-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:dateTime-add-dayTimeDuration
urn:oasis:names:tc:xacml:1.0:function:dateTime-add-yearMonthDuration
urn:oasis:names:tc:xacml:1.0:function:dateTime-subtract-dayTimeDuration
urn:oasis:names:tc:xacml:1.0:function:dateTime-subtract-yearMonthDuration
urn:oasis:names:tc:xacml:1.0:function:date-add-yearMonthDuration
urn:oasis:names:tc:xacml:1.0:function:date-subtract-yearMonthDuration
urn:oasis:names:tc:xacml:1.0:function:string-greater-than
urn:oasis:names:tc:xacml:1.0:function:string-greater-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:string-less-than
urn:oasis:names:tc:xacml:1.0:function:string-less-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:time-greater-than
urn:oasis:names:tc:xacml:1.0:function:time-greater-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:time-less-than
urn:oasis:names:tc:xacml:1.0:function:time-less-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:dateTime-greater-than
urn:oasis:names:tc:xacml:1.0:function:dateTime-greater-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:dateTime-less-than
urn:oasis:names:tc:xacml:1.0:function:dateTime-less-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:date-greater-than
urn:oasis:names:tc:xacml:1.0:function:date-greater-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:date-less-than
urn:oasis:names:tc:xacml:1.0:function:date-less-than-or-equal
urn:oasis:names:tc:xacml:1.0:function:string-one-and-only
urn:oasis:names:tc:xacml:1.0:function:string-bag-size
urn:oasis:names:tc:xacml:1.0:function:string-is-in
urn:oasis:names:tc:xacml:1.0:function:string-bag
urn:oasis:names:tc:xacml:1.0:function:boolean-one-and-only
urn:oasis:names:tc:xacml:1.0:function:boolean-bag-size
urn:oasis:names:tc:xacml:1.0:function:boolean-is-in
urn:oasis:names:tc:xacml:1.0:function:boolean-bag
urn:oasis:names:tc:xacml:1.0:function:integer-one-and-only
urn:oasis:names:tc:xacml:1.0:function:integer-bag-size
urn:oasis:names:tc:xacml:1.0:function:integer-is-in
urn:oasis:names:tc:xacml:1.0:function:integer-bag
urn:oasis:names:tc:xacml:1.0:function:double-one-and-only
urn:oasis:names:tc:xacml:1.0:function:double-bag-size
urn:oasis:names:tc:xacml:1.0:function:double-is-in
urn:oasis:names:tc:xacml:1.0:function:double-bag
urn:oasis:names:tc:xacml:1.0:function:time-one-and-only
urn:oasis:names:tc:xacml:1.0:function:time-bag-size
urn:oasis:names:tc:xacml:1.0:function:time-is-in
urn:oasis:names:tc:xacml:1.0:function:time-bag
urn:oasis:names:tc:xacml:1.0:function:date-one-and-only
urn:oasis:names:tc:xacml:1.0:function:date-bag-size
urn:oasis:names:tc:xacml:1.0:function:date-is-in
urn:oasis:names:tc:xacml:1.0:function:date-bag
urn:oasis:names:tc:xacml:1.0:function:dateTime-one-and-only
urn:oasis:names:tc:xacml:1.0:function:dateTime-bag-size
urn:oasis:names:tc:xacml:1.0:function:dateTime-is-in
urn:oasis:names:tc:xacml:1.0:function:dateTime-bag
urn:oasis:names:tc:xacml:1.0:function:anyURI-one-and-only
urn:oasis:names:tc:xacml:1.0:function:anyURI-bag-size
urn:oasis:names:tc:xacml:1.0:function:anyURI-is-in
urn:oasis:names:tc:xacml:1.0:function:anyURI-bag
urn:oasis:names:tc:xacml:1.0:function:hexBinary-one-and-only
urn:oasis:names:tc:xacml:1.0:function:hexBinary-bag-size
urn:oasis:names:tc:xacml:1.0:function:hexBinary-is-in
urn:oasis:names:tc:xacml:1.0:function:hexBinary-bag
urn:oasis:names:tc:xacml:1.0:function:base64Binary-one-and-only
urn:oasis:names:tc:xacml:1.0:function:base64Binary-bag-size
urn:oasis:names:tc:xacml:1.0:function:base64Binary-is-in
urn:oasis:names:tc:xacml:1.0:function:base64Binary-bag
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-one-and-only
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-bag-size
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-is-in
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-bag
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-one-and-only
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-bag-size
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-is-in
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-bag
urn:oasis:names:tc:xacml:1.0:function:x500Name-one-and-only
urn:oasis:names:tc:xacml:1.0:function:x500Name-bag-size
urn:oasis:names:tc:xacml:1.0:function:x500Name-is-in
urn:oasis:names:tc:xacml:1.0:function:x500Name-bag
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-one-and-only
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-bag-size
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-is-in
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-bag
urn:oasis:names:tc:xacml:1.0:function:any-of
urn:oasis:names:tc:xacml:1.0:function:all-of
urn:oasis:names:tc:xacml:1.0:function:any-of-any
urn:oasis:names:tc:xacml:1.0:function:all-of-any
urn:oasis:names:tc:xacml:1.0:function:any-of-all
urn:oasis:names:tc:xacml:1.0:function:all-of-all
urn:oasis:names:tc:xacml:1.0:function:map
urn:oasis:names:tc:xacml:1.0:function:x500Name-match
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-match
urn:oasis:names:tc:xacml:1.0:function:regexp-string-match
urn:oasis:names:tc:xacml:1.0:function:xpath-node-count O
urn:oasis:names:tc:xacml:1.0:function:xpath-node-equal O
urn:oasis:names:tc:xacml:1.0:function:xpath-node-match O
urn:oasis:names:tc:xacml:1.0:function:string-intersection
urn:oasis:names:tc:xacml:1.0:function:string-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:string-union
urn:oasis:names:tc:xacml:1.0:function:string-subset
urn:oasis:names:tc:xacml:1.0:function:string-set-equals
urn:oasis:names:tc:xacml:1.0:function:boolean-intersection
urn:oasis:names:tc:xacml:1.0:function:boolean-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:boolean-union
urn:oasis:names:tc:xacml:1.0:function:boolean-subset
urn:oasis:names:tc:xacml:1.0:function:boolean-set-equals
urn:oasis:names:tc:xacml:1.0:function:integer-intersection
urn:oasis:names:tc:xacml:1.0:function:integer-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:integer-union
urn:oasis:names:tc:xacml:1.0:function:integer-subset
urn:oasis:names:tc:xacml:1.0:function:integer-set-equals
urn:oasis:names:tc:xacml:1.0:function:double-intersection
urn:oasis:names:tc:xacml:1.0:function:double-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:double-union
urn:oasis:names:tc:xacml:1.0:function:double-subset
urn:oasis:names:tc:xacml:1.0:function:double-set-equals
urn:oasis:names:tc:xacml:1.0:function:time-intersection
urn:oasis:names:tc:xacml:1.0:function:time-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:time-union
urn:oasis:names:tc:xacml:1.0:function:time-subset
urn:oasis:names:tc:xacml:1.0:function:time-set-equals
urn:oasis:names:tc:xacml:1.0:function:date-intersection
urn:oasis:names:tc:xacml:1.0:function:date-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:date-union
urn:oasis:names:tc:xacml:1.0:function:date-subset
urn:oasis:names:tc:xacml:1.0:function:date-set-equals
urn:oasis:names:tc:xacml:1.0:function:dateTime-intersection
urn:oasis:names:tc:xacml:1.0:function:dateTime-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:dateTime-union
urn:oasis:names:tc:xacml:1.0:function:dateTime-subset
urn:oasis:names:tc:xacml:1.0:function:dateTime-set-equals
urn:oasis:names:tc:xacml:1.0:function:anyURI-intersection
urn:oasis:names:tc:xacml:1.0:function:anyURI-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:anyURI-union
urn:oasis:names:tc:xacml:1.0:function:anyURI-subset
urn:oasis:names:tc:xacml:1.0:function:anyURI-set-equals
urn:oasis:names:tc:xacml:1.0:function:hexBinary-intersection
urn:oasis:names:tc:xacml:1.0:function:hexBinary-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:hexBinary-union
urn:oasis:names:tc:xacml:1.0:function:hexBinary-subset
urn:oasis:names:tc:xacml:1.0:function:hexBinary-set-equals
urn:oasis:names:tc:xacml:1.0:function:base64Binary-intersection
urn:oasis:names:tc:xacml:1.0:function:base64Binary-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:base64Binary-union
urn:oasis:names:tc:xacml:1.0:function:base64Binary-subset
urn:oasis:names:tc:xacml:1.0:function:base64Binary-set-equals
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-intersection
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-union
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-subset
urn:oasis:names:tc:xacml:1.0:function:dayTimeDuration-set-equals
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-intersection
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-at-least-one-
member-of
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-union
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-subset
urn:oasis:names:tc:xacml:1.0:function:yearMonthDuration-set-equals
urn:oasis:names:tc:xacml:1.0:function:x500Name-intersection
urn:oasis:names:tc:xacml:1.0:function:x500Name-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:x500Name-union
urn:oasis:names:tc:xacml:1.0:function:x500Name-subset
urn:oasis:names:tc:xacml:1.0:function:x500Name-set-equals
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-intersection
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-at-least-one-member-of
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-union
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-subset
urn:oasis:names:tc:xacml:1.0:function:rfc822Name-set-equals
Appendix C. Example XACML policy implementing simple access control table
Access control table
Roles Analyst CustomerGuest Admin
ContrExp 1 0 0 0
ContrInstr 1 0 0 1
ViewExp 1 1 1 0
ViewArch 1 1 0 1
AdminTsk 0 0 0 1
StartSession 1 0 0 0
StopSession 1 0 0 1
JoinSession 1 1 1 0
Example policy in XACML fomat analytic/CNL2policyXACML00.xml